Secure Cloud Transitions Start with Infrastructure Reviews

There's a temptation to view the many flavors of cloud as the solution to all an enterprise's network, storage, and infrastructure challenges. But simply transitioning existing processes to the cloud without scrutinizing every element from a security perspective compounds current vulnerabilities and creates new problems.
Despite the risks, between 40 percent and 60 percent of enterprises today do not always review these processes before moving to cloud, according to CompTIA's Trends in Information Security Study, published March 2015. Risks include security gaps; moving some processes back to on-premise systems, or switching cloud providers – time-consuming, expensive, and sometimes risky.
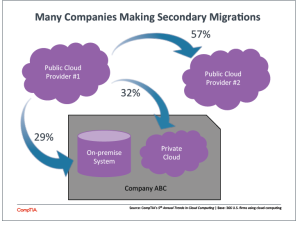
In fact, 60 percent of those organizations that moved back to on-premise systems from cloud cited security as the driver behind their reversal, according to CompTIA's Fifth Annual Trends in Cloud Computing study, released November 2014. Other reasons included failure to integrate (27 percent) and failure to achieve cost goals (23 percent), found the report by the organization of information communications and technology service companies.
To transition successfully – and securely – businesses must understand their own security baseline before inking any cloud contracts, CompTIA wrote in the Information Security report.
"A lot of companies are moving back out of the cloud for some of their systems. Some [companies] … are doing security research after the fact and they want a tighter level of security than a cloud provider can deliver," said Seth Robinson, director of technology analysis at CompTIA, in an interview. "If you can do that ahead of time, then you can avoid doing that back and forth. That’s not to say cloud is bad for all systems. It's far from it. Enterprises need to make that decision on what level of protection they want. Even then, there may be a way to provide the level of security they want in the cloud. Understanding those things upfront will help them ask the right questions and help them understand the right models for their business."
It's vital for IT and business departments to work together to define security requirements, Eric Chiu, founder and president of HyTrust, told Enterprise Technology.
"Cloud, overall, is a fundamental change to IT, technologically and operationally," he said. "The best organizations are the ones that look at virtualization, private cloud, and public cloud holistically with both the infrastructure team and the security team present. They achieve long term goals over time; they're not starting with an insecure environment because they want to get started quickly. If companies don't look at the long-term goal and they don't invest in the security and the infrastructure teams, at some point issues come up."
Security Conscious
It's challenging, cloud executives agree, but assessing an organization's processes, what they are designed to achieve, and the corporate infrastructure provide IT with a snapshot of vulnerabilities and critical assets. Mobile devices add to the mix of vulnerabilities – and cloud benefits.
"Your IT landscape is complex, and often inherited. There are storage systems, servers, private cloud management tools, log managers, backup tools, and many more solutions already deployed in the enterprise. The CompTIA study calls attention to the number of employees taking their work home; IT departments should keep mobile capabilities top of mind when moving to the cloud," Matt Richard, vice president, products, at on-premise enterprise file sync and share platform ownCloud told Enterprise Technology. "Enterprise users want to be able to access important corporate data at any time, from any place. It is important for IT departments to choose a system that allows organizations to maintain ownership and control of their data while enabling collaboration and on-the-go productivity that is demanded by their workforce."
These appraisals are not over and done, either, executives cautioned. Businesses must continually evaluate their networks to ensure systems and data remain safeguarded, said Steve Hultquist, chief evangelist at security analytics company RedSeal, via email.
"Taking the time to analyze the complete network and determine the current state of security and continuing to analyze it as an enterprise expands into cloud systems is challenging, but provides necessary insights into the reality of the situation," he said. "While this is a difficult shift for some to make, doing so creates clarity that allows the broad team to work together to secure the infrastructure, and through that effort, to secure the enterprise as a whole."
Auditing business processes prior to evaluating a cloud transition, allows enterprises to catch any workarounds individuals or departments have created. These roughshod measures can inadvertently create security vulnerabilities or run afoul of legislation, said Diane Clay, director of product marketing at ownCloud.
"Workarounds, which can cause un-intentioned security lapses, are rarely caused by evil intent. IT is often being forced to do more with less – which means that they can’t be experts on everything, and the impacts to the business are rarely fully understood. Done correctly, security overlays good business processes and reinforces them. When processes are broken and no longer work to support the business from new implementations then personnel will take action and implement the workarounds that inadvertently create security weaknesses," she said. "Enterprise IT departments need to find secure alternative solutions that meet the needs of the enterprise and its users and still offer the security mandated by law and good IT practice."
By providing insight, IT also can perhaps simplify overly complex processes, automate more procedures, and consolidate some tasks, said RedSeal's Hultquist.
"Complexity drives an interesting set of responses, from operating according to assumptions that don’t actually hold true to turning a blind eye to reality in an effort to create plausible deniability. Making the effort to uncover the hidden truths allows enterprises to operate in the open, make sure that all of their processes and workflows engage with reality, and that the technologies they deploy are operating accurately and in the right locations," he said. "While this is a difficult shift for some to make, doing so creates clarity that allows the broad team to work together to secure the infrastructure, and through that effort, to secure the enterprise as a whole."
Related
Managing editor of Enterprise Technology. I've been covering tech and business for many years, for publications such as InformationWeek, Baseline Magazine, and Florida Today. A native Brit and longtime Yankees fan, I live with my husband, daughter, and two cats on the Space Coast in Florida.